14/02/14
Project to develop 'next generation' of the Internet is part of Google's broader obsession with speed, CFO says
SAN FRANCISCO – Google is working on technology that will provide data transfer speeds over the Internet that are many times faster than its current Google Fiber service in Kansas City, an executive at the online search giant said on Wednesday.
Google Fiber offers data transfer speeds of 1 gigabit per second currently. But the company is already working on speeds of 10 gigabits per second, Chief Financial Officer Patrick Pichette said during the Goldman Sachs Technology and Internet conference.
Pichette called this the next generation of the Internet and said it was part of Google's broader, long-term obsession with speed.
Faster speeds will increase the use of software as a service because users will be able to trust that critical applications that are data intensive will run smoothly over the Internet, he explained.
"That's where the world is going. It's going to happen," Pichette said. It may happen over a decade, but "why wouldn't we make it available in three years? That's what we're working on. There's no need to wait," he added.
Google is not the only one working on this. Last year, researchers in the U.K. announced that they achieved data transmission speeds of 10 gigabits per second using "li-fi" a wireless Internet connectivity technology that uses light.
Pichette has experience in this area. From early 2001 until July 2008, he was an executive at Bell Canada, which offers a fast, fiber optic Internet service to homes in that country.
Google Fiber is currently available in Kansas City, but Google has said it is bringing the service to Austin, Texas and Pichette told analysts last year that the project is not a hobby for the company.
On Wednesday he was asked whether Google Fiber will be coming to more cities. "Stay tuned," Pichette answered.
Form is loading...
On the heels of proposed California legislation, federal lawmakers also get on board with a bill requiring security features on all cell phones.
Lawmakers' bids to require a smartphone "kill switch" seem to be gaining momentum.
Following the proposal of a California bill, a handful of senators have now proposed federal legislation to require carriers to provide a security feature on all cell phones that would render the devices inoperable if stolen.
The Smartphone Theft Prevention Act is being led by Amy Klobuchar (D-Minn.), along with three other senators, Barbara Mikulski (D-Md.), Richard Blumenthal (D-Conn.), and Mazie Hirono (D-Hawaii). The idea is for users to be able to de-activate and remotely wipe their personal information from their phones if lost or stolen. This kill switch would be free to users.
"Cell phone theft has become a big business for thieves looking to cash in on these devices and any valuable information they contain, costing consumers more than $30 billion every year and endangering countless theft victims," Klobuchar said in a statement. "This legislation will help eliminate the incentives for criminals to target smartphones by empowering victims to take steps to keep their information private; protect their identity and finances; and render the phone inoperable to the thieves."
You must be logged in to see the comments. Log in now!
If you have no account yet, you can register now...
(It only takes a few seconds!)
Form is loading...
23/01/14
Summary: Think you have a Facebook virus or your account has been hacked? Here are four things you should try: reclaim your account, change your password, remove suspicious apps, and perform a virus scan.
You've just discovered your Facebook account has been posting all kinds of weird, pornographic, or generally inappropriate content to your Wall and/or News Feed. Your friends are annoyed with all the questionable posts and requests coming from you.
Did you forget to log out of Facebook at your friend's house, did you accidentally click on something you shouldn't have, or has your account been hacked?
I can't answer these questions without actually seeing what's happening on your profile, but I can offer some advice. Here are four things you should try in order to clean up your Facebook account.
Reclaim your account
If you can no longer login to Facebook, you'll want to follow these instructions from the Facebook Help Center:
-----------
My account is hacked. If your account is sending out spam (ex: advertisements or suspicious links) or was taken over by someone else, secure it here.
----------
After you've navigated to facebook.com/hacked, click the blue "Continue" button and follow the instructions.
Change your Facebook password
It's possible your Facebook woes are coming from the result of a phishing scam. Someone may have created a fake website that looks like Facebook or another online service you visit and tricked you into logging in. Their goal was to steal your password and other account credentials, and they may have succeeded. In this case, you should change your password on Facebook.
If you don't know how to do so, you can refer to the following guide: How to change your Facebook password.
If changing your password fixes your Facebook problems, you should change your password for all your other services too, especially if you use the same password for them as you previously used on Facebook. If this doesn't fix the problem, try the next step.
Remove unwanted Facebook apps
It's possible your Facebook woes are coming from a rogue app that you accidentally installed or were tricked into installing. Every Facebook app has certain permissions to your account. Some of these permissions you can modify, while others you cannot. Your best bet is to remove all the Facebook apps you find suspicious.
If you don't know how to do so, you can refer to the following guide: How to clean up your Facebook apps.
If cleaning out your apps fixes your Facebook problems, tell your friends they should do the same (chances are the app asked your friends to install it as well). If this doesn't fix the problem, try the next step.
Get some security software and run a virus scan
It's possible your Facebook woes are coming from some sort of malware, be it a keylogger, a trojan, or some other type of virus. Even if you think your computer is clean, it can't hurt to check.
I recommend Microsoft Security Essentials –it's free and gets the job done very well. Another good one is Malwarebytes. Other free alternatives include Avira and Avast.
The aforementioned security programs are for Windows. If you have a Mac, try using the antivirus from Sophos.
After running the virus scan, clean out whatever the program detects. If you're not sure about what it found, ask a friend who might or give us a ring on 07889413011.
You must be logged in to see the comments. Log in now!
If you have no account yet, you can register now...
(It only takes a few seconds!)
Form is loading...
22/01/14
BACKGROUND - Nude pictures, unknown bills, weird Apps - we are seduced continuously with links we should Click. Well you should NOT!!!!
10 dangerous links to avoid.
The Web is one hell of a seductive place. Cyber wizards try to tickle your interest with links that look interesting or important, but they actually transfer you to landing pages filled with malware. Or they send you to pages inviting you to enter your username and password. Social engineering is the way they spread malware. Do NOT get Fooled!!! Below I will mention 10 different type of links you should NEVER Click.
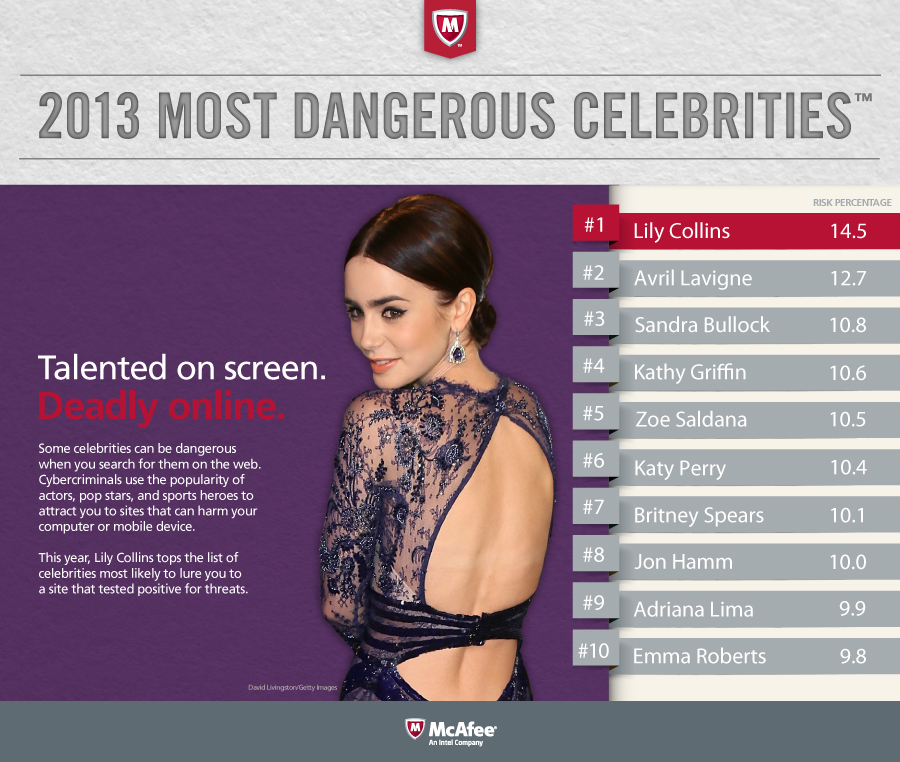
1. Celebrities
Cybercriminals try to lure their victims with promises of juicy details about Celebrities. Or with Free Apps connecting to these Celebrities. Every year a list of top 10 names, which contain the most dangerous links, is published. "Lily Collins" has been named as the most dangerous Celebrity of 2013, according to McAfee.
2. Breaking!
Phishers (mis)use our curiosity by publishing "News" stories that we feel we need to know about. In the Aftermath of every Tsunami a enormous wave of spam mail follows. After every Bombing a explosion of Link traffic occurs. And after the death of a Celebrity, it rains with fake messages and malicious links.
Breaking News of a unknown source is dangerous, especially if it spread through the Social Media and you can't directly determine the source. Malware creators jump on the bandwagon quicker and smarter then ever before, through the use of SEO-Tricks they send us superfast to their "News".
3. Unknown software
We all know or are aware of not installing unknown software on our computers. We also know we should only download programmes from trusted sources. But why are we not using the same vigilance when using mobile devices?
How many Android-user tick the box "Downloads from unknown sources allowed" and subsequently download unwanted rubbish? Some Malware act like a legitimate app. Always double check what your downloading and always stick to the official app store. There is enough mobile malware out there, that will make your mobile send SMS to premium numbers, steal your passwords or setup your Android-device to be used by a botnet.
4. Free downloads
If you navigate the dark ally's of the internet, you must be prepared to be attacked. Criminals will lure you with free porn, Licence codes for software or illegally uploaded movies or music. But when you start to download it goes wrong.
There Aint No Such Thing As A Free Lunch.
Both, the offered Freebees or the so called "Necessary" download tools may bring malware with them. Now try and get rid of them. Cleaning a PC is not free; It takes a lot off time and expensive cleaning and security tools. And if you infected a device at your Work, it can even cost you your job.
5. Scandals
"Are you aware of the ESSEX sextape with Joey and Sam? No? Here is the link.
Would you be so kind and share this on Twitter and Google+?"
This is the kind of Scandal teasers you shouldn't be eluded to.!!! Remember, if there were a sextape of Joey and Sam then surely it would be on the SUN or any tabloid. And they would not publish this without the link.
6. Bargain Hunting
A Cheap Ipad, a Certificate an Exotic Holiday - erverything is Cheap. Or even better Free. "Congratulations, u are our 1.000.000 Visitor! Click here to claim your Prize" Flashing Banner's
Just ignore and continue surfing. If an offer sounds to good to be true, than it probably is . Here we go once more. And make this your Mantra.
There Aint No Such Thing As A Free Lunch.
7. Attachment with Bill (Credit note).
You'll probably used to receive invoice, credit notes or bills online via email. In June securityfirm Kaspersky detected a incredibly well constructed virus email. It looked to be originated from the respected data-company LexisNexis. Complete with legitimate looking return address and the LexisNexis-logo. The attached PDF "Invoice" was a ZIP file containing a Trojan.
So be prepared to challenge any incoming bills or invoices if you don't expect them.
8. Charities
In the wake of a Natural Disaster people are very quick to donate money for help through various charities. Be vigilant when receiving emails from so called charities, make sure their attached email addresses are correct. If it states Red-Cross check the email is indeed from the Red-Cross. Before you enter you bank account details, check whether the charity is genuine.
9. Exclusive Access
Promised to get "Exclusive Access" to a clip or story, provided you logon with your Facebook-account or one of the other social media site? Unfortunately you will not find the exclusive. You would if it was a "genuine members only" site. If you can't find the clip or story on any of the tabloid sites, believe me you won't find it here.
10. Questionnaires
Don't ask me why, but people enter all kinds of online questionnaires. Or they want to know how other people voted and click on a poll. And the you notice you have to enter personal details before the results are revealed. Even if you just spend five minutes answering questions, you are not going to give personal information to someone you don't know do you? Please stick to sites and sources that you know and Trust.
If you have any questions or you think you system might be affected and need help, give us a call on 07889413011.
You must be logged in to see the comments. Log in now!
If you have no account yet, you can register now...
(It only takes a few seconds!)
Form is loading...
21/01/14
Emails can be dangerous. Reading the contents of an email should be safe if you have the latest security patches, but email attachments can be harmful. Any type of file can be attached to an email, including .exe program files. Many email servers will perform virus scanning and remove potentially dangerous attachments, but you can’t rely on this. Look for the common warning signs so you can avoid viruses, worms, and Trojans.
So-called “spear-phishing campaigns” that go after high-value corporate and government targets have used email attachments to take advantage of previously unknown security vulnerabilities. Email attachments can be dangerous to anyone.
Dangerous File Extensions
The easiest way to identify whether a file is dangerous is by its file extension, which tells you the type of file it is. For example, a file with the .exe file extension is a Windows program and should not be opened. Many email services will block such attachments.
However, .exe isn’t the only type of dangerous file extension. Other potentially dangerous file extensions that can run code include: .msi, .bat, .com, .cmd, .hta, .scr, .pif, .reg, .js, .vbs, .wsf, .cpl, .jar and more. This is not an exhaustive list — there are many different file extensions in Windows that will run code on your computer when executed.
Office files with macros are also potentially dangerous. If an Office document extension ends with an m, it can — and probably does — contain macros. For example, .docx, .xlsx, and .pptx should be safe, while .docm, .xlsm, and .pptm can contain macros and can be harmful. Of course, some businesses use macro-enabled documents. You’ll have to exercise your own judgment.
In general, you should only open files with attachments that you know are safe. For example, .jpg and .png are image files and should be safe. .pdf, .docx, .xlsx, and .pptx are document files and should also be safe — although it’s important to have the latest security patches so malicious types of these files can’t infect you via security holes in Adobe Reader or Microsoft Office.
Archives, Especially Encrypted Ones
In an attempt to make it around email filters, someone may email you malicious file attachments in an archive — especially an encrypted one. For example, you may receive an email with a .zip, .rar, or .7z file and its password. You’d need to download the archive file and extract its contents with the password to access them.
The password-protection — or encryption — on the archive prevents email scanners and antivirus programs from examining it, so it’s very possible that the archive could contain malware. Of course, password-protected archives are also an effective way to email sensitive files. You’ll have to use your judgment once again.
The Sender
Looking at who an email was sent by can help you identify whether an email attachment is malicious or not. Beware: an attachment can be malicious even if you know the sender! If they’ve become infected, a malware program may send you emails from their email address, disguised as emails they’d send.
If you get an email from someone you don’t know with a questionable-looking attachment, it’s probably malware. If you receive a macro-enabled Office document from someone you’re not expecting one from, exercise extreme caution.
On the other hand, if your boss tells you in person that she’ll email you a macro-enabled Excel spreadsheet and you get an email from her with an .xlsm file later that day, the attachment is probably safe.
If you’re not sure whether someone sent you a suspicious-looking email attachment, you may want to give them a phone call or ask them in person. If they didn’t send the attachment, they’ll appreciate the warning that their computer is infected or their email address has been hijacked.
The Email Itself
The email’s contents can also offer clues. If you get an email from someone you know and something seems a bit off, it may be written by malware or a hijacker. Such emails could also be phishing emails without any dangerous attachments — for example, if you get an email from someone you know saying they’re trapped and need you to wire some money with Western Union, this could easily be a phishing scam.
If you get an email from FedEx or UPS and it asks you to download an email attachment and run it, that’s another red flag. Legitimate businesses will never ask you to download and run programs attached to an email.
Antivirus Alerts
If you’re using a webmail service like Gmail, Outlook.com, or Yahoo! Mail, your webmail service will automatically scan incoming attachments for malware and inform you if the attachments are dangerous. Of course, if you see a warning that an attachment is malicious, you should not download it! The text of the email may ask you to ignore any problems and assure you that the attachment is actually fine, but this would likely be a trick.
If you download an email attachment and your desktop antivirus program flags it, stop right there. Don’t click through the warning and run it anyway — trust your antivirus program more than the email attachment.
Bear in mind that antivirus programs aren’t perfect. They’ll miss things occasionally, so you can’t only rely on your antivirus. An attachment could be dangerous even if no antivirus flags it.
Have a Healthy Suspicion
When it comes to email attachments, you should exercise extreme caution and assume the worst. Don’t actually download or run an attachment unless you have a good reason to do so. If you’re not expecting an attachment, treat it with healthy suspicion. If it’s an image attachment, that’s probably okay. PDFs should be okay if you have the latest security patches, too. But if you’re not sure what something is, you shouldn’t run it.
Your webmail client’s preview features can also help. You can preview PDF files, documents, images, and other types of files in your browser without actually downloading them to your computer.
You must be logged in to see the comments. Log in now!
If you have no account yet, you can register now...
(It only takes a few seconds!)
Form is loading...
You must be logged in to see the comments. Log in now!
If you have no account yet, you can register now...
(It only takes a few seconds!)